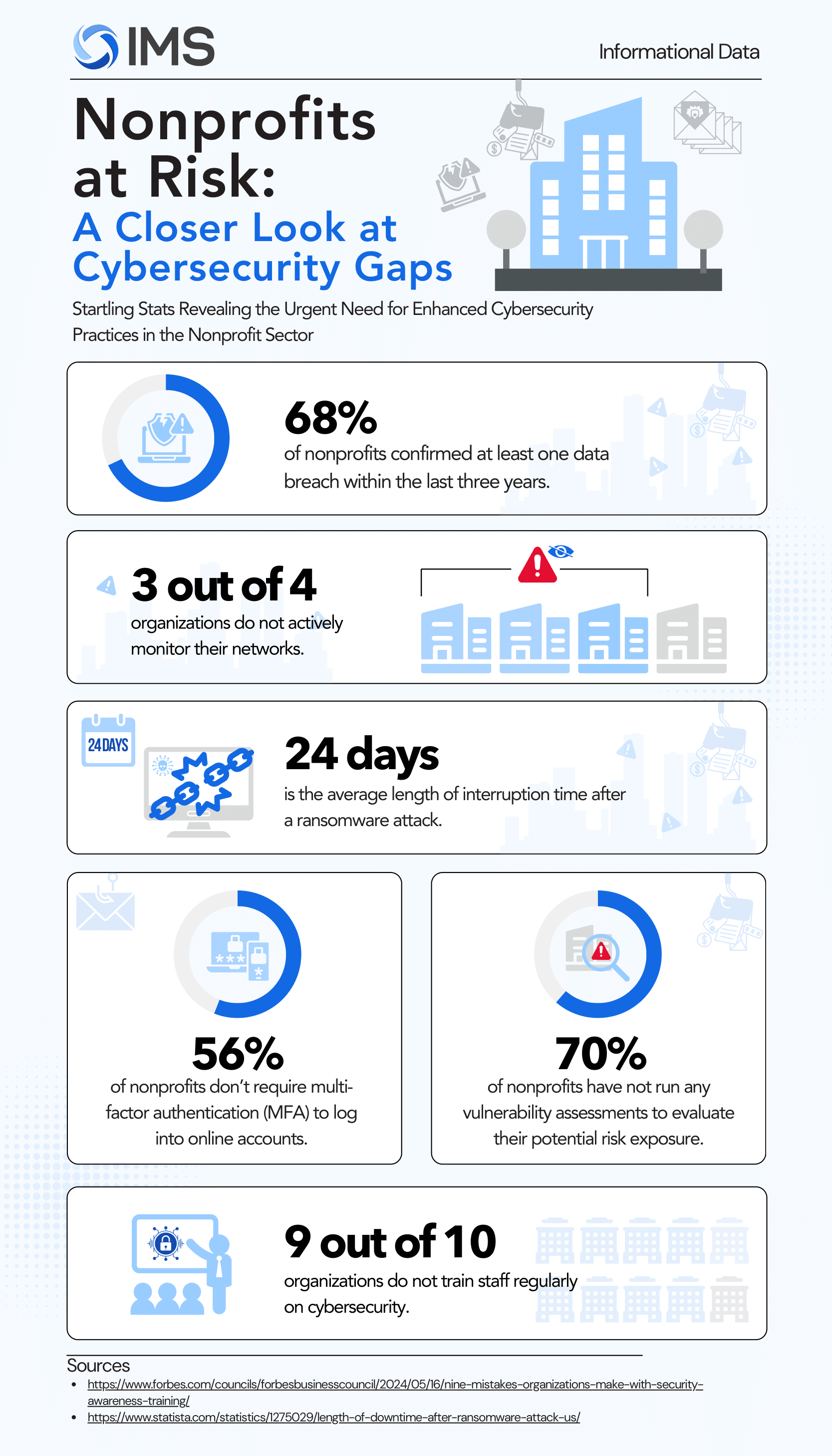
Nonprofits are frequent targets for cyberattacks due to limited resources and reliance on sensitive donor and organizational data. Without a dedicated IT staff or sufficient budgets, many organizations struggle to implement effective security measures, leaving them vulnerable to breaches, ransomware, and other threats. Addressing these gaps is crucial to maintaining donor trust, protecting operational continuity, and ensuring compliance with data protection regulations.
A closer look at the challenges organizations face reveals startling statistics that highlight the urgent need for enhanced security practices. From data breaches and phishing attacks to inadequate monitoring and response plans, the risks are significant. Therefore as a non-profit organization, you must prioritize strengthening your cybersecurity frameworks to safeguard your missions and data effectively.
Common Cybersecurity Risks Nonprofits Face
Nonprofits face unique challenges when securing their systems and data. Here are some of the most common cybersecurity risks you may encounter:
- Limited Budgets for Advanced Security Tools
Many non-profits operate with tight budgets, often unable to invest in advanced cybersecurity tools. Without these tools, you may lack the necessary defenses to protect sensitive data, making your organization more susceptible to attacks. - Phishing Attacks Targeting Volunteers
Volunteers, who may not be well-versed in cybersecurity, are often targets of phishing attacks. These attacks typically trick individuals into revealing sensitive information or clicking malicious links, which can compromise your organization’s security. - No Dedicated IT Staff
Without in-house IT professionals, your organization may struggle to manage and address security risks. This lack of expertise can lead to gaps in security protocols and response plans, leaving your systems vulnerable. - Inadequate Employee Training
If your staff is not regularly trained on cybersecurity best practices, they may unknowingly make errors that compromise security. From weak passwords to mishandling of sensitive information, human error is a significant cause of breaches in non-profit organizations. - Sensitive Donor Data Exposure
Nonprofits handle large volumes of sensitive donor information, which makes them prime targets for hackers. Without proper safeguards in place, you risk exposing this data, which could lead to financial loss and damage to your reputation. - Ransomware Attacks on Donor Databases
Ransomware attacks are increasingly targeting donor databases. Hackers can lock your data and demand payment for its release, disrupting your operations and potentially putting sensitive donor information at risk. - Non-Compliance with Data Protection Regulations
Non-compliance with regulations like GDPR or HIPAA can lead to severe penalties and reputational harm. Your organization must stay up to date with regulatory requirements to avoid costly mistakes and ensure you handle data responsibly. - Weak Incident Response Plans
A poorly defined or underdeveloped incident response plan can significantly delay your recovery in the event of a breach. A quick and efficient response is crucial to minimizing damage and restoring operations as soon as possible. - Lack of Multi-Factor Authentication (MFA)
Not requiring MFA for accessing online accounts increases the risk of unauthorized access. MFA adds an extra layer of security by requiring a second form of verification, reducing the likelihood of hackers gaining entry to your systems. - Outdated Data Storage Practices
Many nonprofits rely on outdated or insecure storage methods, which can increase vulnerability to cyberattacks. Ensuring that your data is stored in secure, encrypted environments is essential for protecting sensitive information from potential breaches.

Step-by-Step Guide to Mitigating Cybersecurity Risks
1. Assess Your Current Cybersecurity Posture
Begin by evaluating your existing security measures to identify potential vulnerabilities. A thorough risk assessment can uncover gaps in employee awareness, data protection practices, and incident response protocols. IMS offers security posture scoring as part of our initial engagement, providing a professional evaluation tailored to your organization’s needs.
After completing the assessment, prioritize improvements based on the level of risk they pose. Focus on areas such as employee training, access controls, and compliance with data protection regulations.
Regularly review and update this assessment to track progress and refine strategies over time.
2. Develop and Implement a Cybersecurity Framework
Establishing a clear and practical cybersecurity framework is essential. This framework should align with your organization’s size, structure, and available resources to ensure a sustainable approach to data protection.
- Set Policies: Define clear rules for acceptable use, data handling, and access controls.
- Assign Roles: Identify team members responsible for specific cybersecurity tasks to foster accountability.
- Use Professional Tools: Leverage trusted solutions to implement robust measures that protect your systems and data effectively.
3. Addressing Targeted Phishing Attacks
Phishing is one of the most common threats for non-profits, often targeting volunteers or staff with limited cybersecurity awareness.
- Training: Regularly educate your team on recognizing phishing tactics, such as suspicious email addresses and urgent requests. Real-world examples can make the training more impactful.
- Verification Protocols: Implement secondary verification processes for financial transactions, such as confirming requests via phone or a separate communication channel.
In 2020, Philabundance, a Philadelphia-based food bank, lost over $923,000 in a phishing scam. Fraudsters sent emails mimicking contractors, directing payments to fraudulent accounts. This incident highlights the financial and reputational damage phishing can cause.
Don’t wait for an issue like this to persist before taking action. We’ve seen how devastating phishing attacks can be for non-profits, both financially and reputationally. By implementing proactive training and verification processes now, you can significantly reduce the risk to your organization.
To help, we’ve created the Spot Phishing Scams with Ease checklist, a simple, actionable guide to help you and your team identify phishing attempts before they cause harm. Download it now and ensure your organization is better equipped to handle these threats.
4. Protect Donor and Organizational Data
Sensitive donor and organizational data are primary targets for cybercriminals, and a breach could result in significant financial loss and loss of trust.
- Data Encryption: Encrypt all sensitive data, including donor information, to protect it from unauthorized access.
- Access Controls: Regularly audit who has access to sensitive data and enforce strict access control policies. Restrict data access to specific roles, and revoke access immediately when an employee leaves.
- Compliance: Review and ensure compliance with regulations such as GDPR or HIPAA to meet legal and regulatory data protection standards.
5. Enhance Authentication and Access Control
Weak or reused passwords remain significant vulnerabilities for non-profits. Strengthen your security by implementing multi-factor authentication (MFA) and strict access control policies.
- MFA: Use free or low-cost tools such as Microsoft Authenticator to implement MFA for all online accounts.
- Access Control: Enforce the principle of least privilege by granting users only the minimum level of access they need to perform their job functions.
- Review Privileges: Regularly audit user privileges and make adjustments based on role changes or staff departures.
6. Build an Incident Response Plan
A well-defined incident response plan ensures quick containment and recovery during a cybersecurity event.
- Incident Identification: Define what constitutes a cybersecurity incident for your organization.
- Containment Procedures: Develop clear steps for isolating affected systems to minimize the damage.
- Recovery Protocols: Outline processes for restoring data from backups and resuming operations.
- Testing: Conduct regular simulations to identify weaknesses in the plan and improve its effectiveness. Templates from organizations like NIST can be a helpful resource.
7. Upgrade IT Infrastructure
Outdated systems and software create entry points for cyberattacks. Keeping your IT infrastructure up to date is crucial for minimizing vulnerabilities.
- Update and Patch: Regularly apply updates and patches to your systems to close known security vulnerabilities.
- Cloud Solutions: Transition to cloud-based solutions like Google Drive or Microsoft OneDrive for Business, which offer integrated security features and are easier to maintain.
- Replace Unsupported Systems: Replace outdated or unsupported systems to avoid unpatchable vulnerabilities.
By following these steps, your organization can significantly reduce cybersecurity risks, protect your data, and enhance operational resilience. These measures are key to safeguarding your mission from the threats posed by cybercriminals.

Safeguarding Your Non-Profit from Cybersecurity Threats
Cyberattacks threaten your operations, donor trust, and sensitive data. Non-profits often face limited resources, but building a strong defense is essential. Proactive cybersecurity measures protect your data and maintain donor and volunteer trust, ensuring your mission continues without disruption.
IMS Solutions helps non-profits create robust, cost-effective security frameworks with expert guidance and scalable tools. From network monitoring to staff training, IMS provides tailored, proactive support to address vulnerabilities. Don’t wait for a breach—partner with us to safeguard your mission. Contact us today to secure your organization’s future.